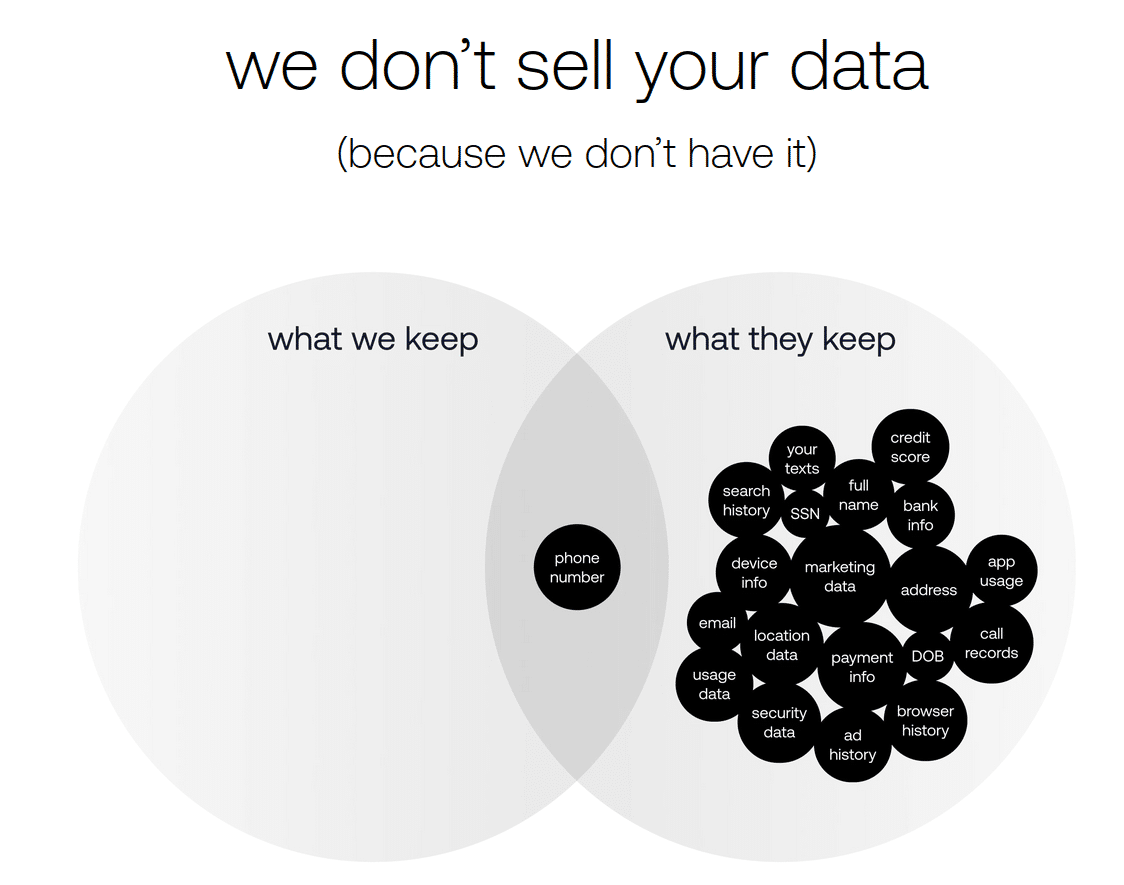
REALLY Wireless is a new cell carrier backed by significant venture capital funding. The carrier aggressively touts its focus on privacy. One of the first visuals on REALLY’s homepage makes the pitch:
Trackers, Trackers Everywhere
On that same homepage, I find a bunch of trackers from companies like:
- Fullstory
Not only is REALLY collecting a bunch of data in the “what they keep” section of its diagram, but it’s also giving the data to third parties.
Spy-Proof?
Not all data collection by cell carriers is nefarious. Information about a device and its location is necessary to make cell service work. Further, laws often compel carriers to share specific information with certain entities. When a 911 call is placed from a cell phone, carriers must help emergency services locate the caller.
In 2022, a company called INVISIV launched PGPP (Pretty Good Phone Privacy). The idea was to prevent tracking of users’ locations via their phones’ IMSI numbers. The product got some press since it was technically and intellectually interesting. It narrowly focused on just one type of data collection. INVISIV didn’t pretend the product was a perfect remedy for even that single type of data collection.
REALLY, however, is happy to make audacious claims. Here’s another visual from the homepage:

Come on. If REALLY came up with technology that made users immune to spying, security researchers and federal agents would be knocking on REALLY’s door (or perhaps breaking it down).
Be Better
Here’s one last visual from REALLY’s homepage:

I have some advice for REALLY if it’s trying to make the planet a better place.
STOP LYING.